
The Kerberos Authentication System. Brad Karp UCL Computer Science. CS GZ03 / M030 17 th November, 2008. Why Study Kerberos?. One of most widely used authentication systems, implemented in many, many UNIXes for a variety of services

clarissa + Follow
Download PresentationAn Image/Link below is provided (as is) to download presentation Download Policy: Content on the Website is provided to you AS IS for your information and personal use and may not be sold / licensed / shared on other websites without getting consent from its author. Content is provided to you AS IS for your information and personal use only. Download presentation by click this link. While downloading, if for some reason you are not able to download a presentation, the publisher may have deleted the file from their server. During download, if you can't get a presentation, the file might be deleted by the publisher.

Kerberos: A Network Authentication Tool. Seth Orr University of Missouri – St. Louis CS 5780 System Administration. Overview. Introduction History Components Protocol Installation and Configuration Strengths and Weaknesses Conclusions References. Introduction. Security
474 views • 31 slides

Abstract:. Windows 2000 implements kerberos version 5 with extensions for publickey authentication.The kerberos client is implemented as a security provider through the Secutiry Service Provider Interface.Initial authentication is intergrated with winlogon single sign-on architecture.The Kerberos
777 views • 32 slides

Information System Security AABFS-Jordan Summer 2006 Kerberos Authentication Protocol. Supervisor :Dr. Lo'ai Ali Tawalbeh Done by: Wa’el Musa Hadi . Using Kerberos the fundamentals. Computer/Network Security needs:. Authentication Who is requesting access Authorization
352 views • 18 slides

Week 7: Authentication Applications Kerberos . Kerberos. X.509. How To Secure Network. How do you secure your network and each workstation or server with one tool?. How To Secure Network.
712 views • 56 slides

Kerberos – Private Key System. Ahmad Ibrahim. History. Cerberus, the hound of Hades, (Kerberos in Greek ) Developed at MIT in the mid 1980s Available as open source or supported commercial software. Combination of topics covered previously in class. What do we want to do?.
357 views • 22 slides
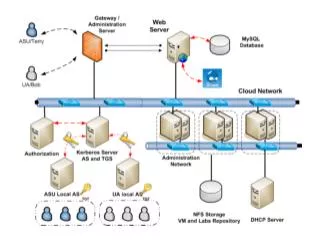
Kerberos Authentication for Multi-organization. Cross-Realm Kerberos Authentication. User sent request to local Authentication Server Local AS shares cross-realm key to verifier's authentication server(VAS) Local AS sent TGT to client User request a session key with his/her TGT
312 views • 5 slides

Kerberos Authentication Systems. KERBEROS. In Greek mythology, a many headed dog, the guardian of the entrance of Hades (Hell). Outline. Authentication in Campus Kerberos 4 Realms (Domains) under Kerberos 4. Authentication in Campus. Workstations, Servers are distributed
571 views • 31 slides

Kerberos Authentication. Kerberos . Requires shared secret with KDC ( perhaps not for PKINIT) Shared session key established Time synchronization needed Mutual Authentication Credentials allow impersonation. Authorization.
288 views • 9 slides

Chapter 5 Authentication Applications Kerberos . Kerberos. X.509. How To Secure Network. How do you secure your network and each workstation or server with one tool?. How To Secure Network.
733 views • 56 slides

Iliano Cervesato, Aaron D. Jaggard, Andre Scedrov, and Chris Walstad Supported by ONR, NSF, NRL. Specifying Kerberos 5 Cross-Realm Authentication. Outline. Introduction Kerberos 5 Formalization Properties Vulnerabilities. Overview of Results.
389 views • 23 slides

Week 7: Authentication Applications Kerberos. Kerberos. X.509. How To Secure Network. How do you secure your network and each workstation or server with one tool?. How To Secure Network.
704 views • 56 slides

Kerberos Authentication. Alternative to one time passwords. Need for an authentication scheme which never sends the passwords in clear text form over the network.
356 views • 21 slides

Authentication of Kerberos and Wireless Communication. Kerberos AMPS IS-95 : A-Key GSM DECT Bluetooth 802.11b. Kerberos. Abbreviation of Kerberos and Two Simple Types of Authentication Dialogue. Abbreviation :. C = client TGS = ticket-granting server
560 views • 37 slides

Authentication and Authorization Infrastructures: Kerberos vs. PKI. PD Dr. Rolf Oppliger eSECURITY Te chnologies Rolf Oppliger ( www.esec u rity.ch) Thunstra sse 57b, CH-3074 Muri, Switzerla nd E-Mail: ro lf.oppliger@esecur ity .ch Te l. +41 (0)79 654 84 37. Agenda. 1. Introduction
520 views • 38 slides

Kerberos Authentication Systems. KERBEROS. In Greek mythology, a many headed dog, the guardian of the entrance of Hades (Hell). Outline. Authentication in Campus Kerberos 4 Realms (Domains) under Kerberos 4 Appendix: Kerberos 5. Authentication in Campus.
786 views • 44 slides

Integrating PKI and Kerberos Authentication services. Alberto Pace. Authentication Methods. Two technologies for authentication Kerberos and X.509 Certificates (PKI) Today at CERN Kerberos is used in Windows Domains and AFS
425 views • 32 slides

Cross cell AFS authentication using Kerberos 5. HEPiX-HEPNT Vancouver, October 21 st 2003 Enrico M.V. Fasanelli. Agenda. Why? Theory and practice on Kerberos5 cross realm transitive hierarchical authentication AFS cross cell authentication K5 @ INFN.IT Last minute tests Future.
314 views • 20 slides

Kerberos A network authentication protocol. Nick Parker CS372 Computer Networks. Introduction. Kerberos Network Authentication Protocol Mutual Network Authentication Project Athena Collaborative effort amongst MIT, Digital, and IBM Support interoperability within large scale networks
373 views • 15 slides

Authentication Applications: Kerberos, X.509 and Certificates . 2003700691 REYHAN AYDO Ğ AN. Outl ine. Introduction to KERBEROS How Kerberos works? Comparison between version 4 and 5 Certificates X.509 Directory Authentication Service Conclusion.
847 views • 47 slides

Authentication & Kerberos. User Authentication. fundamental security building block basis of access control & user accountability is the process of verifying an identity claimed by or for a system entity has two steps: identification - specify identifier
482 views • 27 slides

Kerberos Authentication. Kerberos. Requires shared secret with KDC ( perhaps not for PKINIT) Shared session key established Time synchronization needed Mutual Authentication Credentials allow impersonation. Authorization. How does the authentication mechanism fit in authorization topology
235 views • 9 slides

The Kerberos Authentication System. Brad Karp UCL Computer Science. CS GZ03 / 4030 26 th November, 2007. Why Study Kerberos?. One of most widely used authentication systems, implemented in many, many UNIXes for a variety of services
156 views • 15 slides